What Is Two-Factor Authentication (2FA) and Why Does it Matter? What is two-factor authentication (2FA) and why does it matter? If you are unfamiliar with this extra layer of protection for all of your logins, keep reading. It’s no secret that we live in a time where access to laptops and smartphones is so prevalent. […]
Zoom Scrambles to Address Cybersecurity Issues in Meeting Platform As the usage of Zoom has skyrocketed during the coronavirus outbreak, the company has had to respond quickly to security flaws and potential phishing attacks As Zoom usage skyrockets around the world, so too do the opportunities to exploit users unfamiliar with the tool. The […]
How to Create a Work-From-Home Team Quickly As Your Business Deals With the Coronavirus Stay productive and secure your tech network as you deal with the coronavirus. Get support for at-home employees. Learn how to switch from an in-office to a remote team. In the midst of the coronavirus, business owners are facing a […]
Everything You Should Know About Two Factor Authentication Does your business use 2FA? With the prevalence of data breaches today, it’s time to start employing this simple security feature within your business. Without a doubt, you’ve read and heard about the rampant cybersecurity problems that are insidiously plaguing businesses today. Municipalities in places like […]
Working From Home Due to Coronavirus? Consider These Tips If you’re suddenly working from home due to the coronavirus, maximize productivity with a dedicated workspace, enjoyable breaks, and engagement with colleagues. For the vast numbers of Americans suddenly barred from their offices due to the coronavirus pandemic, working from home can pose significant challenges. […]
When considering the employee and employer benefits of working remotely, businesses are wise to change. The alternative could make your outfit less competitive. If you would like to gain a little perspective on how radically our culture has changed, try this exercise. Pick up a pencil and a piece of paper and write out […]
Hackers Target Businesses Concerned Over COVID-19 Hackers are capitalizing on fear and concern related to coronavirus to launch ransomware and malware attacks. Here’s how to protect your business and employees. As the COVID-19 spreads worldwide, hackers are taking advantage of an already stressed and strained healthcare system to attack vulnerable companies. Phishing attacks are on […]
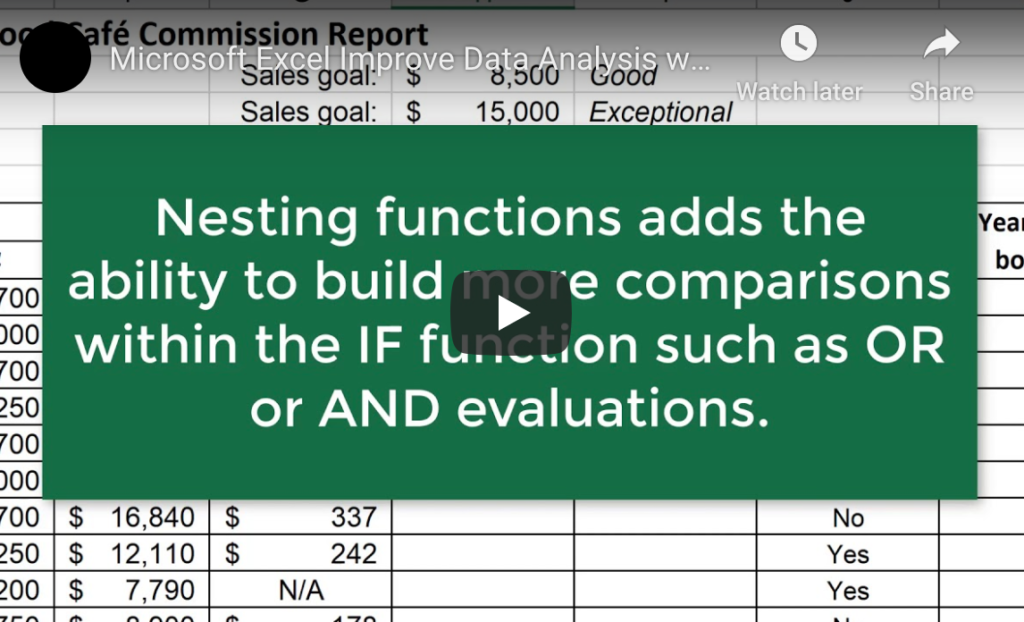
Improving Data Analysis with the IF Function in Microsoft Excel Have you ever wondered what the IF Function in Microsoft Excel actually does? Here we explore a few top tips for making it save you time while evaluating data. There’s no doubt that Microsoft Excel is a robust program. Companies all over the globe […]
Protect Yourself – Use Two-Factor Authentication for Your Business Learn about what two-factor authentication is and how it works. Once you understand its benefits you will see how helpful it could be for your business. Two-factor authentication is something every business should be using to protect themselves and their customers. You know the […]
Has Your Business Fallen Behind In Its Incident Response Strategy? Incident Response plans are proving to be a key element in data breach recovery. That’s why proactive industry leaders are adding and updating these strategies. Entrepreneurs and other decision-makers are acutely aware that doing business in the digital age requires robust cybersecurity. Most companies […]